Enhancing Cloud Security: Integrating Risk Management, IT Audit/Compliance (including SOC 2), and AI for Optimal Protection
Enhancing Cloud Security: Integrating Risk Management, IT Audit/Compliance (including SOC 2), and AI for Optimal Protection
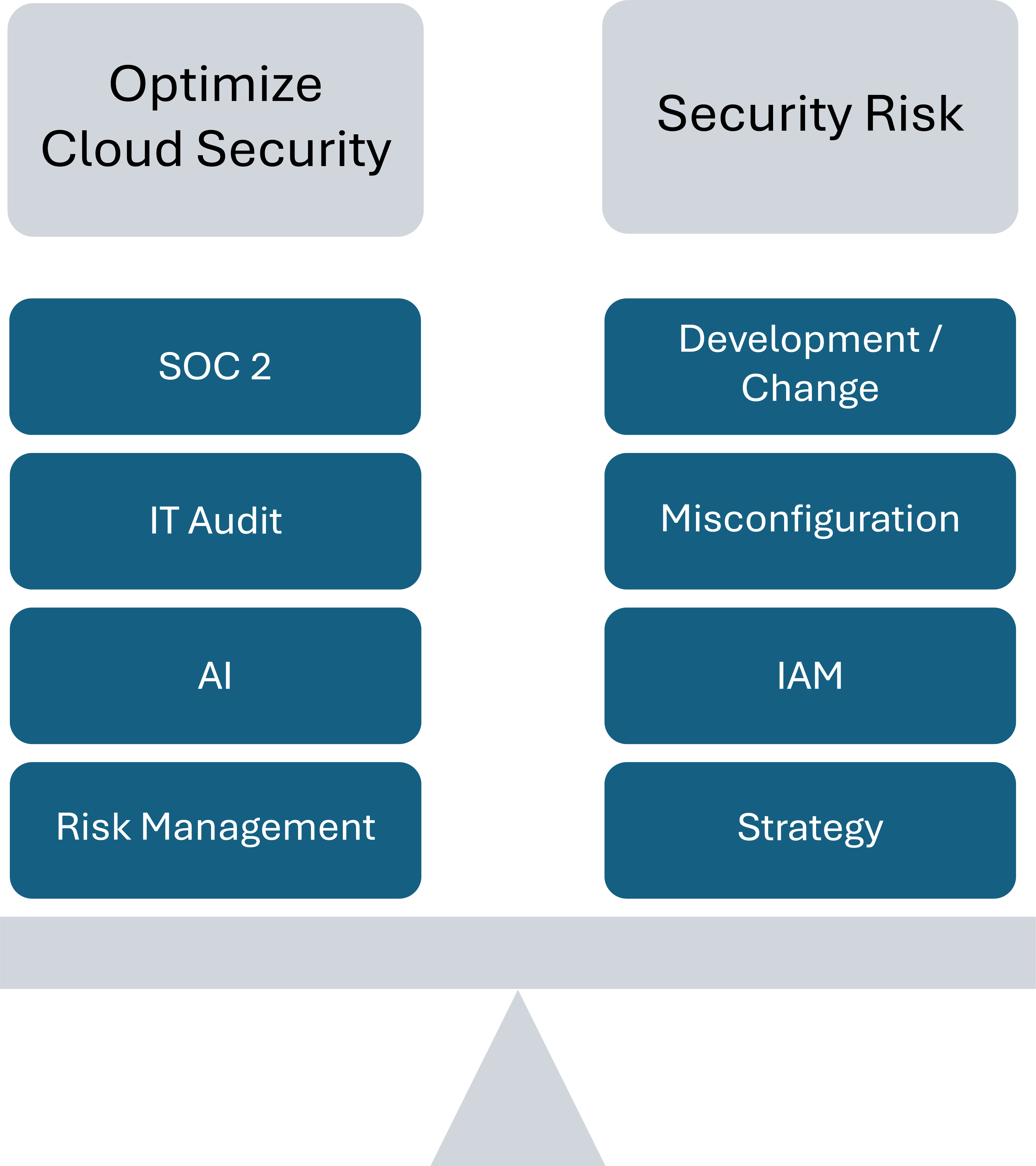
The Cloud Security Alliance (CSA) recently released its “Top Threats to Cloud Computing 2024,” which highlights the top 11 cloud threats based on a survey from over 500 industry experts. This article will specifically focus on 5 of the 11 security issues:
- Misconfiguration & Inadequate Change Control
- Identity & Access Management (IAM)
- Inadequate Selection/ Implementation of Cloud Security Strategy
- Insecure Software Development
- System Vulnerabilities
We will also discuss how to mitigate those security issues through:
- Risk management
- IT Audit/Compliance (including SOC 2®)
- Artificial intelligence (AI)
Misconfiguration & Inadequate Change Control
Misconfigurations and inadequate change control were noted as the top cloud threat for 2024, followed by identity and access management. Let’s first address misconfigurations and change management and the impact these threats can have on cloud computing.
Misconfigurations can occur in a number of areas, including access control which can lead to breaches, unauthorized access, and insecure network design. Misconfigurations can typically be traced back to inadequate planning and design during the initial phases of the Software Development Lifecycle. The issue of misconfiguring cloud infrastructure has led Microsoft (Azure), Amazon (AWS), and Google (GCP) to publish frameworks that assist organizations in evaluating the various decisions they have to make while architecting their cloud environments.
Inadequate change management is another area of concern that has led to several negative headlines for large organizations that have failed to properly assess changes prior to putting them into production. Not only can inadequate change control processes lead to system downtime, but they can also allow vulnerabilities to exist in code and remain undetected until that vulnerability is ultimately exploited by a nefarious threat actor.
Identity & Access Management
IAM is another security issue that is closely tied to misconfiguration and inadequate change control. Failing to properly implement, configure, update, and monitor IAM can lead to several problems down the road. Overly permissive access privileges, lack of an identity lifecycle, failure to implement segregation of duties, and failure to detail a comprehensive IAM strategy are four common issues that can create to a negative outcomes for an organization.
Inadequate Cloud Security Strategy
According to the CSA, “Cloud security strategy encompasses considering external factors, existing implementation, and selection of cloud technologies, priorities, and trends toward creating a high-level plan or approach. These insights help organizations achieve cloud security goals and support business objectives,” (p.22).
Devising a proper cloud security strategy prior to system design and development can help ensure that security is baked in from the start, as opposed to trying to implement it after cloud services have been constructed. Developing a sound cloud security strategy will also assist organizations by ensuring proper planning for methods to address security challenges and confirming that the strategy is connected back to business goals and objectives.
Insecure Software Development
Organizations that fail to implement a secure development lifecycle risk delivering a cloud application that has not been properly designed, developed, and tested. Insecure software can lead to vulnerabilities being introduced, which can then be exploited by threat actors to compromise an organization’s cloud environment. Defining and implementing a secure development lifecycle and using “Well Architected Framework” documents from cloud service providers will assist organizations with creating plans to identify weaknesses and vulnerabilities, and to develop more secure applications.
System Vulnerabilities
The CSA outlines four main system vulnerabilities: misconfiguration, zero-day vulnerabilities, unpatched software, and weak or default credentials. According to the National Security Agency (NSA), of these four items, misconfiguration is the most widespread cloud vulnerability.
To deal with the vast number of system vulnerabilities, organizations need to develop a vulnerability management program that is tied to their cloud security strategy and their secure development lifecycle. Additionally, conduct continuous monitoring, vulnerability scanning, and penetration testing regularly to identify system vulnerabilities. Once vulnerabilities have been discovered, address them in accordance with policies and procedures, and a documented change management process.
Integrating Risk Management, IT Audit/Compliance (including SOC 2), and AI for Optimal Protection
Now that we have covered each security issue, it is time to highlight how risk management, IT Audit / Compliance [including System and Organization Controls (SOC) 2® ] and artificial intelligence integrate to provide optimal protection over these top security concerns.
Risk Management
Assess the risk to your business with full consideration of changing technology (such as the use of AI), the boundaries of responsibility, and shared accountability, likelihood, impact, and velocity. This is your foundation to plan for risk mitigation and tolerance, which will drive your decision-making relating to defining your security controls and approach to securing your use of the cloud. Also, identify controls related to configuration and change control, IAM, cloud security strategy, software development, and system vulnerabilities.Artificial Intelligence
As attacks continue to become more sophisticated and configuring cloud environments becomes more challenging, organizations should evaluate mitigation strategies that can help reduce the risk and impact of security issues and the administrative overhead on their personnel. One solution that appears to have promise is the strategic implementation of AI.
Let’s now look at how AI can be used strategically to address some of the security concerns outlined above:
- Misconfiguration & Inadequate Change Control:
- Utilize machine learning to automatically detect and alert on misconfigurations based on a defined baseline
- Insecure Software Development:
- Automate various steps, such as code review and vulnerability analysis, to identify issues before a product is deployed into production
- System Vulnerabilities:
- Implement AI-powered offensive security tools to discover vulnerabilities in cloud configurations, protocols, and Application Program Interfaces (APIs) to stay ahead of threats
IT Audit and SOC 2
The CSA recommends that organizations undergo independent audit and assurance assessments at a minimum of once per year to provide assurance to stakeholders that controls are operating as intended and are in alignment with business goals and objectives. This assurance can come in the form of an IT Audit for your internal use or an SOC Cybersecurity Report for your management or board of director’s use performed by an independent auditor. Furthermore, if your organization provides services to other companies, you can also obtain assurance in the form of an SOC 2 report that can be used by your management and user base.
The RubinBrown Difference
As an AICPA peer-reviewed firm, RubinBrown specializes in comprehensive compliance and assessment services tailored to the unique needs of our clients. Our team of experts leverages industry-leading frameworks and best practices to deliver thorough, actionable insights to key stakeholders. Whether you’re seeking an IT Audit, an AI HealthCheck, a Cybersecurity HealthCheck, a SOC 2 Report, a security framework assessment, or an IT risk assessment, the professionals at RubinBrown are here to assist.
Published: 11/04/2024
Readers should not act upon information presented without individual professional consultation.
Any federal tax advice contained in this communication (including any attachments): (i) is intended for your use only; (ii) is based on the accuracy and completeness of the facts you have provided us; and (iii) may not be relied upon to avoid penalties.
.png)